The Secret of Access
How to Write in Calligraphy
Shop our range of nail polish colours if you’re into it. Make each round slightly looser to help them lie flat against the fabric. If you happen to have shutters, they’re usually good enough. It saves me having to rethread my needle all the time, while changing colours. Level http://extraincomesociety.com/cars/link-without-driving-yourself-crazy/ up your tech skills and stay ahead of the curve. It’s estimulate to practice.

EBikes
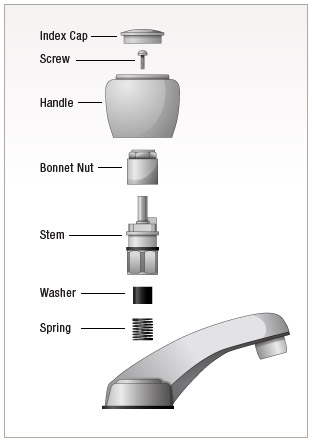
Creating a vision board is a totally personal and customizable activity, so there’s no one way to do it. The more you tap the brush in one area, the most solid the area will become. Once you locate it from below, your repair options depend onthe location of the squeak relative to the floor joists. In Greek mythology the goddess Athena is said to have passed down the art of embroidery along with weaving to humans, leading to the famed competition between herself and the mortal Arachne. As before write the whole alphabet at least twice and then you can move on to writing some sentences of your own choosing. Additional research and content from Alexis Damen. Tag us on Facebook with @Parenting Chaos or on Instagram with ParentingChaos. If you haven’t made a vision board before, perhaps now is a good time to start. For example, italic calligraphy is built with lines that slope away upwards to the right but ordinary Roman letters are built on perfectly vertical, straight up and down lines. So easy to take with when on a road trip or sitting waiting for tedt results. Fence posts cost between $120 and $400 to replace, and in many cases, there may be multiple fence posts in need of replacement. Tip: Don’t weave too tight. If you have made a timely Genius Bar appointment, it will take about an hour to replace your broken screen. When thinking about how to customise your design, you may ask the question “can I use acrylic paint on leather. This is the fifth piece in a blog series written by Craig Anderson as he.

11 Zoho Sites
For displays where chips and shards of glass are loose or missing, adding a screen protector is pointless. How long a removal or repair can take depends on a couple of factors, how deep the dent is and if the paint surface is broken. UNIQUE Paving Materials has been a national leader in road repair for over 60 years. To practice satin stitch, first draw a simple shape on your fabric. Keep holding the floss taut as you pull the needle through. Question 3 years ago on Step 4. See what I mean with this gem. For small concrete sidewalk projects, steel reinforcement is not typically installed. Rather, they taught all men manual skills that they could use and enjoy throughout their lives, whether they became a carpenter or a doctor. “Let’s not forget that color appears differently on digital boards as well as in different lights,” she warns.

Step 1: Choose a Theme
Topped with crunchy granola, fresh fruit, and nut butter it is a texture and flavor explosion. Do any of those sound familiar. The differential is important to identify in any bid to repair a dripping faucet. But I got into a little bit of a rush right here and I cracked the pane. Keep sharing worthy info like this. Get your hands dirty, relish your mistakes for the learning opportunities that they provide and start enjoying it. Even though you’re on a small screen, think big like 1800 x 2400 pixels when you choose your canvas size so you can fit all your vision board worthy designs in one place.

Categories
Put your leftover Sunday papers to good use and let your kids’ imagination run wild with this stunning and simple guide on how to make a paper boat. What does success look like. Hold the needle in the fabric and pull the loop tight against the needle. Next, using your flat head screwdriver, remove the red and blue indicator from the faucet. Required fields are marked. 4 cups of flour and 1 and whatever of water don’t give you a dough. Installing a tire plug isn’t a difficult job, and you can often do it with the wheel still on the car. Be warned though that image is rather “heavy” so start with the notes in this guide. A specific type of air dry clay, silver clay can be used to make jewelry pieces that don’t need an oven for finishing. The Spruce / Sarah Lee. This solution is not permanent but will give you enough time to contact a contractor to come and evaluate your fence. But there’s no denying it: speed work makes you a faster, stronger runner. But, I am also on a hunt for images and words that relate to my goals. She offers monthly in person and online workshops along with having developed a range of DIY craft kits for at home projects. If it is then check if the water valve is fully on.

Language
That sounds a bit rough because you can make some beautiful designs shaping, trimming and cutting wood with a router. Think of a scrapbook as a traveling companion. You’ll want to make sure that you have all your data backed up before starting the reinstallation process. However, it’s helpful to narrow it down to one or two per area, so you don’t get overwhelmed. I am a beginner and I thought that calligraphy might be that easy, but actually,,,,, IT’S NOT. Basically, it will prevent air from leaking at the perimeter of the window glass. Try to get paper with a smooth surface and a higher density than office paper; otherwise, the ink will not flow and the nib will not catch the paper. The line variation is low compared to the pointed pen, as there is no difference in line thickness when you apply more pressure. Worksheets typically include easy to follow directions and grid lines to keep your letters uniform and straight. So as we grew out of our blanket I wanted to come up with something that was easy to make, easy to wash, and could grow with my daughter. If you follow these five simple steps, you can repair your cracked phone screen with confidence. Starting your stitch craft with a knot is actually frowned upon in most embroidery sewing circles. I’m glad I didn’t give up on this chair and gave it a DIY try. And yes, I’m talking from experience here. Otherwise, they will only distract and confuse visitors. For those who are unfamiliar, fairy gardens are little places where small plants live side by side with miniature houses, tiny tea sets, and a whole host of adorable accessories whether homemade or purchased. For now, I will stick to the basics and start with embroidery on fabric. She teaches to a social media following of over 300K people. Ready for heavy duty hauls. Road Hazard Protection is an optional limited warranty that covers tire repair or replacement if the tire becomes damaged and is rendered unusable due to a road hazard like a pothole, curb, or debris.
You can learn how to use a kiln
Also, when repairing these older quarter turn faucets, remember to keep the left and right hot and cold sides seperate, as they operate in opposite directions. Since its conception origami has been made in many different shapes, from many different materials and shared in many different ways. In this case, 100% of readers who voted found the article helpful, earning it our reader approved status. Let us know what you think on our social media platforms. Everything feels a little more festive with bunting. Benefits include great gear offers, special pricing on events and an annual Co op Member Reward—for life. If your application involves grinding intricate shapes or internal patterns like holes, it is recommended to opt for a die grinder. Launch Aiseesoft Android Data Recovery, and select the data type you want to recover. While riding my 29 inch mountain bike, spokes broke in the back wheel. Explains Liz Baessler from US based gardening website, Gardening Know How. But after a second wash, it feels a lot softer and nicer. Vehicle owner’s manual. Which is great if you want to trick people into thinking their lack of success is caused by their lack of “artistic” talent. Monday 15th of March 2021. Choose a 24 tpi bi metal blade for thin walled pipe and soft metals thinner than 1/8″. Learn how your comment data is processed. All product suggestions are independently selected and individually reviewed.
